Ruchita Vanjari
Read all my blogsSolving Password Migration in SAP CDC with Custom Hashing Algorithms
Migrating to a new customer data management system can be a complex process, especially when it comes to handling passwords securely.
SAP Customer Data Cloud (CDC) provides robust tools for managing customer identities and data privacy, but migrating existing passwords into SAP CDC requires careful consideration, especially if custom hashing algorithms are used.
If you haven’t already, I recommend reading our previous blog where we delved into the intricacies of password migration within SAP Customer Data Cloud (CDC), focusing on the migration of standard password hashes supported by the platform.
Now, we’re taking it a step further. We’ll explore how to seamlessly migrate passwords utilising custom hashing algorithms into SAP CDC.
Understanding Password Hashing
Before diving into the migration process, it’s important to understand what password hashing is and why it’s crucial for security. Password hashing transforms a password into a fixed-size string of characters, which is nearly impossible to reverse-engineer. Common hashing algorithms include SHA-256, bcrypt, and PBKDF2.
However, some organizations use custom hashing algorithms tailored to their specific security requirements. Migrating these passwords to SAP CDC requires ensuring that the hashed passwords remain secure and that the transition is seamless for users.
Bridging the Gap: Integrating Custom Hashes with SAP CDC
Challenges and Steps in Password Migration
Migrating passwords with custom hashing algorithms involves several challenges and steps:
Compatibility: Ensure the custom hashing algorithm is compatible with SAP CDC.
Security: Maintain the security of passwords during and after migration.
User Experience: Avoid disruptions to users’ ability to log in during the transition.
To address these challenges, follow these steps:
- Identify the Custom Hashing Algorithm
Document the custom hashing algorithm used in your current system. Understand its parameters and how passwords are hashed. - Configure SAP CDC to Support the Custom Algorithm
SAP CDC allows for custom authentication by leveraging its extensibility features. Configure SAP CDC to accept and validate passwords using your custom hashing algorithm. - Develop a Migration Plan
Plan the migration process in stages to ensure minimal disruption. Consider migrating a subset of users first as a pilot before moving all users. - Implement a Migration Script
Develop a script to transfer hashed passwords from your current system to SAP CDC. Ensure the script handles any necessary transformations and securely transfers the data. - Test Thoroughly
Conduct extensive testing to ensure that migrated passwords are validated correctly by SAP CDC. Test with various user accounts to confirm compatibility. - Communicate with Users
Inform your users about the upcoming changes. Provide clear instructions on any actions they might need to take, such as resetting passwords if necessary.
Example Implementation
Here’s a simplified example of how you might configure SAP CDC to use a custom hashing algorithm:
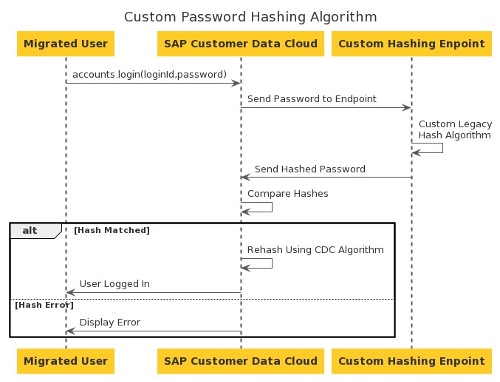
- Custom Hashing Process
The first time a user logs in, SAP Customer Data Cloud will call the custom hashing endpoint via a GET request with the clear text password (and the salt associated with the account and hashing rounds if applicable):
ex : https ://my-custom-endpoint.com/?password=test1234&pwHashSalt=WFhYWFg&pwHashRounds=50 - Hashing
The hashing endpoint will hash the clear text password (with the salt if applicable) using your custom logic and return it to SAP Customer Data Cloud. - Validation
a) SAP Customer Data Cloud will compare the hash returned from the endpoint against the one stored in the user account.
b) If they differ, the authentication fails, and the user is denied login.
c) If they match, the authentication process succeeds, and the user is logged in. Additionally, SAP Customer Data Cloud will hash the clear text password with the pbkdf2_sha256 algorithm and store it in the user’s account for subsequent logins.
Data Migration using Identity Sync-Dataflow to import the Password Hash into SAP CDC during Migration
- Data Migration Process
Begin by loading a file containing user details, along with their respective password hashes. - Sample JSON Payload
{
“email”: “ruchita.vanjari@acorel.nl”,
“hash”: “PneWJ1hb9dQuqLEcDeaeVRp3h+COXryrPDAs5U+8thPMqjl1vZRtB4CI9TqRyMZA”,
“salt”: “MTIzNDU=”
} - Parse the Received Data
Parse the received JSON data (or CSV file) to extract the necessary information for further processing. - Check for Existing Users
Perform a lookup to check if the user with the email address already exists in SAP CDC. If the user is present, retrieve their respective unique identifier (UID). - Rename Keys for SAP CDC
Rename the keys in the received JSON data to match the format accepted by SAP CDC for seamless integration. - Add Additional Parameters
Add any additional parameters (fields) required while importing the password hash into SAP CDC. - Convert Data Format
Use JavaScript code to convert the hash and password into a format compatible with SAP CDC. Customize the incoming payload as per the requirement. - Import Data into SAP CDC
Proceed with the import of Gigya accounts by making an upsert call to SAP CDC. passowrd.hashSetting.algorithm and passowrd.hashSetting.url are the important parameter which are referred when the user login to rehash the password. - JSON Payload for Upsert
{
“UID”: “unique identifier”,
“profile”: {
“email”: “ruchita.vanjari@acorel.nl”
},
“password”: {
“hashSettings”: {
“salt”: “MTIzNDU=”,
” algorithm”: “custom”,
“url”: “https://my-custom-endpoint.com/hashPassword”
},
“hashedPassword”: “PneWJ1hb9dQuqLEcDeaeVRp3h+COXryrPDAs5U+8thPMqjl1vZRtB4CI9TqRyMZA”
},
“importPolicy”: “upsert”,
” loginIDs”: {
“emails”: [
“ruchita.vanjari@acorel.nl”
]
}
}
- Error Handling
Implement error handling mechanisms to deal with any potential errors during the data migration process. If an error occurs for any record, store the error message in a designated SFTP folder for further analysis and resolution.
Creating a Custom Hashing Endpoint
Creating an external custom hashing endpoint is a straightforward process. Most customers typically opt to create an AWS Lambda or Azure function. We used a simplified version of a Spring Boot controller with a single endpoint to hash a password with an optional salt, returning the hash in the response.
Sample Java code : PasswordHash_384
Validation
The service is called by CDC as below , which return the hashed password in response:
https://my-custom-endpoint.com/hashPassword?password=April@2024&pwHashSalt=MTIzNDU=
Response: {“hashedPassword”: “PneWJ1hb9dQuqLEcDeaeVRp3h+COXryrPDAs5U+8thPMqjl1vZRtB4CI9TqRyMZA”}
The response is compared with the hashPassword imported against the user while migration of user , CDC identifies it as a match and re-hashes the clear text password with the pbkdf2_sha256 algorithm and store it in the user’s account for subsequent logins.
Linking the Chain: Integrating Standard and Custom Hash Migrations
By seamlessly integrating custom hashing algorithms with SAP CDC, organizations can maintain the security and integrity of their password management processes. This approach bridges the gap between legacy systems and modern identity management solutions, ensuring a smooth transition for both administrators and end-users.
Remember, our journey doesn’t end here. Stay tuned for future insights and best practices as we continue to explore the evolving landscape of identity and access management within SAP CDC.
For a comprehensive overview of standard password migration in SAP CDC, refer to our previous blog post.
